Glacier Vault Access Policy allows you to control access to your vaults, for instance,
grant access to your vaults to another users, protect your data from accidental deletion, etc.
To Edit Vault Access Policy
1. Start FastGlacier and navigate to the vault you want to work with.
2. Click Vaults, Advanced, Access Policy
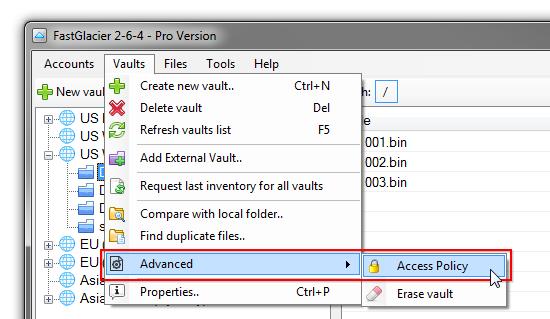
Click Vaults, Advanced, Access Policy to open Access Policy Editor
Vault Access Policy Editor will open:
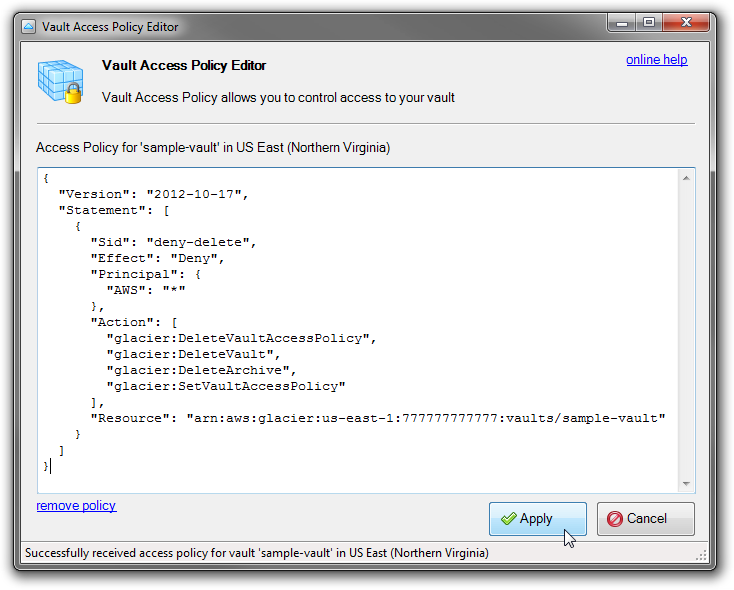
Vault Access Policy Editor
3. Enter the policy document and click Apply:
Vault Access Policy Examples
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "cross-account-upload",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111111111111:root"
},
"Action": [
"glacier:InitiateMultipartUpload",
"glacier:ListParts",
"glacier:UploadArchive",
"glacier:UploadMultipartPart",
"glacier:AbortMultipartUpload",
"glacier:CompleteMultipartUpload"
],
"Resource": "arn:aws:glacier:us-west-2:777777777777:vaults/DailyBackup"
}
]
}
Allow uploads to the vault DailyBackup in US-West Oregon region for user with account id 111111111111
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "deny-delete",
"Effect": "Deny",
"Principal": {
"AWS": "*"
},
"Action": [
"glacier:DeleteVaultAccessPolicy",
"glacier:DeleteVault",
"glacier:DeleteArchive",
"glacier:SetVaultAccessPolicy"
],
"Resource": "arn:aws:glacier:us-east-1:777777777777:vaults/sample-vault"
}
]
}
Deny data deletion and access policy change for all users on the vault sample-vault
{
"Version":"2012-10-17",
"Statement":[
{
"Sid": "read-only-for-everyone",
"Principal": "*",
"Effect": "Allow",
"Action": [
"glacier:InitiateJob",
"glacier:GetJobOutput"
],
"Resource": [
"arn:aws:glacier:us-west-2:777777777777:vaults/shared-vault"
]
}
]
}
Grant Read-Only Permission to all AWS Accounts for the vault shared-vault
You can find more information about vault access policy language and policy examples in AWS Documentation.
